Difference between revisions of "WEP Cracking"
| Line 25: | Line 25: | ||
You may wish to record the channel of your target network. | You may wish to record the channel of your target network. | ||
| − | == | + | ==Putting the wireless interface in monitor mode == |
| + | |||
| + | These instructions assume that you are using Kali Linux. | ||
| + | |||
| + | First we must connect the USB directly to our Kali VM. Click VM at the top of your virtual machines. You will click: | ||
| − | + | VM->Removeable Devices->Realtek 802.11n NIC->connect | |
| − | + | Issue a: | |
| − | + | sudo ifconfig -a | |
| − | + | Identify which is your wireless interface name. It will probably be wlan0. | |
| − | |||
| − | + | Issue an: | |
| + | |||
| + | lsusb | ||
| + | |||
| + | You should see a line describing the Realtek netork adapter. Now, we need to compile the driver against your kernel headers. | ||
| + | |||
| + | Install the required build tools: | ||
| + | |||
| + | sudo apt install git dkms bc | ||
| + | |||
| + | Clone the Git repo | ||
| + | |||
| + | git clone https://github.com/morrownr/8812au.git | ||
| + | |||
| + | Cd into the directory | ||
| − | + | cd 8812au | |
| − | + | Compile | |
| − | + | make | |
| − | + | Then install | |
| − | sudo | + | sudo make install |
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Now reboot your Kali virtual machine. Now, when you log back in, you must strictly follow the instructions below to get a reliable monitor mode. Do this one line at a time. | |
| − | sudo rfkill unblock all | + | sudo ifconfig wlan0 up # Make sure the interface is down |
| − | sudo | + | sudo airmon-ng check kill # Kill things that might interfere with the process |
| + | sudo iwconfig wlan1 mode monitor # put it in monitor mode | ||
| + | sudo rfkill unblock all # Make sure there are no hardware bocks | ||
| + | sudo iwconfig wlan1 channel 1 # Set the channel | ||
| + | sudo ifconfig wlan1 up # Bring the interface back up | ||
==Collecting Weak ivs== | ==Collecting Weak ivs== | ||
Revision as of 01:44, 23 July 2021
Decrypting packets and/or accessing someone’s network without their consent is illegal. The purpose of this lab is not to encourage students to break into vulnerable networks, rather it is hoped that students will:
- Gain an appreciation of the specific technical vulnerabilities in WEP. This should help to make an informed decision about appropriate security measures to implement in your own or your employer’s wireless networks.
- Have sufficient understanding of the tools involved to be able to test your own network's security.
We will be using aircrack-ng. We want to encourage your interest in network and computer security but do NOT use the tools or techniques that you learn in this lab on networks that are not your own. Do NOT attempt to use any of the tools on the Murdoch University infrastructure.
Contents
Lab Setup
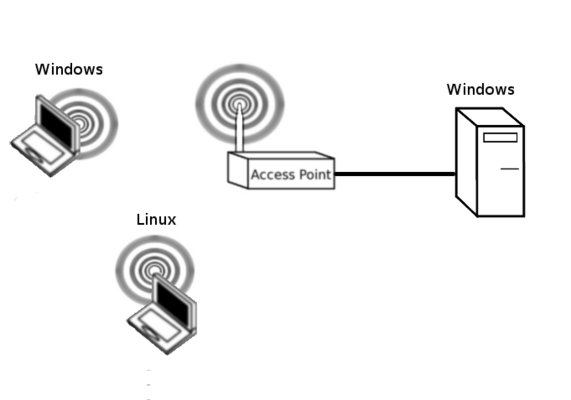
You should start by setting up a network as shown below.
Configure WEP
Our first task is to configure WEP over the wireless network. Please ensure that you keep the username as root and the password as admin. You can use any hex key that you like. Please be aware that using a WEP passphrase will still use the generated hex key for encryption. Ensure that the wireless Windows PC can Ping the Wired PC. Refer to Basic AP Configuration if you need to. Share a file over the network to generate traffic. Additionally, turn off the 5GHz radio and change the network mode on the 2.4 GHz radio to 802.11b/g only.
Your Linux based PC will capture as many packets as possible and try to decrypt the key. WEP cracking tools rely on capturing enough data to enable you to launch statistical attacks on the key. So, we will use two tools, airodump for capturing packets and aircrack for launching our statistical attack on the key.
Before you start, try scanning the local LAN using the following command:
nmcli d wifi
You may wish to record the channel of your target network.
Putting the wireless interface in monitor mode
These instructions assume that you are using Kali Linux.
First we must connect the USB directly to our Kali VM. Click VM at the top of your virtual machines. You will click:
VM->Removeable Devices->Realtek 802.11n NIC->connect
Issue a:
sudo ifconfig -a
Identify which is your wireless interface name. It will probably be wlan0.
Issue an:
lsusb
You should see a line describing the Realtek netork adapter. Now, we need to compile the driver against your kernel headers.
Install the required build tools:
sudo apt install git dkms bc
Clone the Git repo
git clone https://github.com/morrownr/8812au.git
Cd into the directory
cd 8812au
Compile
make
Then install
sudo make install
Now reboot your Kali virtual machine. Now, when you log back in, you must strictly follow the instructions below to get a reliable monitor mode. Do this one line at a time.
sudo ifconfig wlan0 up # Make sure the interface is down sudo airmon-ng check kill # Kill things that might interfere with the process sudo iwconfig wlan1 mode monitor # put it in monitor mode sudo rfkill unblock all # Make sure there are no hardware bocks sudo iwconfig wlan1 channel 1 # Set the channel sudo ifconfig wlan1 up # Bring the interface back up
Collecting Weak ivs
Using Wireshark
Try capturing the encrypted packets in Wireshark. What filters do you need to ensure you have 50000 data packets? Save the pcap on the Desktop.
Using Aerodump
Another alternative is using airodump. Type:
sudo airodump-ng [interface_name] --ivs -w [filename] --channel [x]
That command will start airodump and save the ivs to the filename you give it.
You should see the frame count increasing and the SSID of the lab test network should be visible. While you wait to capture sufficient packets try setting up another client (if available) to associate with the AP once you have discovered the key.
Cracking the WEP key
50,000 or less should defeat 40 bit encryption. While you are waiting, do some research of your own. Research the technical reasons why WEP failed.
Once you think you have enough IVS. Press ctrl+c on the keyboard to exit airodump. We are now going to try to crack the key with aircrack. Type:
sudo aircrack-ng [filename]
Now that you have the key. Capture some transmissions across the WEP network. Use Wireshark to decrypt the frames and then investigate what was transmitted. You will find that most web transactions are encrypted with SSL/TLS, but usually, DNS messages are in cleartext.
Questions
If a malicious user has cracked a WEP key, what threat does this pose to the network? To help you answer this question, how likely is it that banking/email accounts of the network users will be compromised? What danger does a compromised WEP key pose to the network infrastructure? Why does an attack from a compromised WEP key pose a greater threat than an attack from the Internet? How does WPA with TKIP overcome the problems with WEP?
Challenge
The keys you have just cracked were likely easy to crack because you were deliberately creating a lot of wireless traffic. Most of the time, APs sit dormant which means that you would need to wait a very, very long time to collect enough packets to crack the key.
It is possible to generate traffic for a wireless network without prior knowledge of the key by identifying an encrypted ARP packet. ARP packets are 68 bytes in length so, in a wireless environment, we can capture the ARP packet, identify it based on the length and then replay it back into the network. The network will respond with ARP replies, generating traffic.
To setup your ARP station, on an additional PC, type:
aireplay-ng --arpreplay -b <bssid MAC address> -h <source MAC address> <interface>
http://www.aircrack-ng.org/doku.php?id=i_am_injecting_but_the_ivs_don_t_increase
Eventually, this program will identify an ARP packet and the begin replaying them into the network to generate traffic.
“In order for an access point to accept a packet, the source MAC address must already be associated. If the source MAC address you are injecting is not associated then the AP ignores the packet and sends out a “DeAuthentication” packet. In this state, no new IVs are created because the AP is ignoring all the injected packets.” - Jay Usher (Past student)