Difference between revisions of "Crack the Code"
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | [[File:Marissa_Mayer.jpg|right|300px|thumbnail|Marissa Ann Mayer Former President & CEO, Yahoo Image: [https://www.flickr.com/photos/40040706561@N01/ Michael Tippet] [https://creativecommons.org/licenses/by-sa/2.0/ Attribution-ShareAlike 2.0 Generic (CC BY-SA 2.0)] ] | + | [[File:Marissa_Mayer.jpg|right|300px|thumbnail|Marissa Ann Mayer Former President & CEO, Yahoo Image: [https://www.flickr.com/photos/40040706561@N01/ Michael Tippet] [https://creativecommons.org/licenses/by-sa/2.0/ Attribution-ShareAlike 2.0 Generic (CC BY-SA 2.0)] ]] |
Your goal is to decipher the following email. You suspect that this is a cypher, where the letters have been individually rearranged. We know that the communications came from Marissa Ann Mayer, an American information technology executive, who worked at Google and served as the president and CEO of Yahoo! | Your goal is to decipher the following email. You suspect that this is a cypher, where the letters have been individually rearranged. We know that the communications came from Marissa Ann Mayer, an American information technology executive, who worked at Google and served as the president and CEO of Yahoo! | ||
<pre> | <pre> | ||
| Line 21: | Line 21: | ||
While cryptography has moved on from simple substitution cyphers, the types of techniques used in this activity, such as statistical analysis, social engineering and making educated guesses about the content are components of many successful cyber attacks today. | While cryptography has moved on from simple substitution cyphers, the types of techniques used in this activity, such as statistical analysis, social engineering and making educated guesses about the content are components of many successful cyber attacks today. | ||
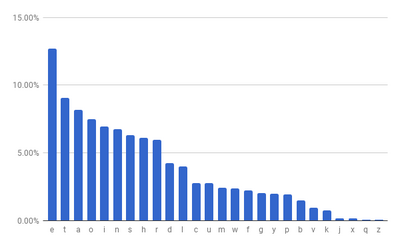
| − | [[File:distribution_seen_in_english.png|left| | + | [[File:distribution_seen_in_english.png|left|400px|thumbnail|Relative frequencies in English text]] |
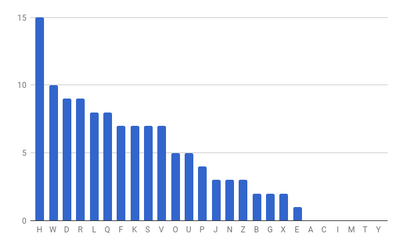
| − | [[File:distrubution_seen_in_code.png|right| | + | [[File:distrubution_seen_in_code.png|right|400px|thumbnail|Actual occurance of characters seen in code]] |
Latest revision as of 01:29, 26 September 2023

Your goal is to decipher the following email. You suspect that this is a cypher, where the letters have been individually rearranged. We know that the communications came from Marissa Ann Mayer, an American information technology executive, who worked at Google and served as the president and CEO of Yahoo!
Zkhq shrsoh wklqn derxw frpsxwhu vflhqfh, wkhb lpdjlqh shrsoh zlwk srfnhw surwhfwruv dqg wklfn jodvvhv zkr frgh doo qljkw. Pdulvvd Dqq Pdbhu
You know that this is a sentence in English and are directed to look at the distribution of single letter frequency below. Some analysis has also been performed on the code with the frequency of characters arranged and plotted.
There are some other common combinations in the English language.
- The most common doubles: ss ee ll tt ff mm oo
- The most common first letters of a word: t o a w b c d
- Order of frequency of final letters in a word: e s t d n r
Hint: Pay attention to both the analysis of text as well as the information that has been provided about the email.
While cryptography has moved on from simple substitution cyphers, the types of techniques used in this activity, such as statistical analysis, social engineering and making educated guesses about the content are components of many successful cyber attacks today.