Difference between revisions of "EVE NAT"
| Line 349: | Line 349: | ||
frame-relay lmi-type ansi | frame-relay lmi-type ansi | ||
! | ! | ||
| − | router | + | router osp 1 |
| − | + | net 192.168.0.0 0.0.255.255 area 0 | |
| − | + | default-information originate | |
! | ! | ||
ip nat inside source list NAT interface Serial1/0 overload | ip nat inside source list NAT interface Serial1/0 overload | ||
Latest revision as of 08:13, 4 May 2020
Contents
- 1 Learning Objectives
- 2 Scenario
- 3 Steps
- 4 Network Address Translation (NAT)
- 5 Configure Static NAT
- 5.1 Configure Dynamic NAT with a Pool of Addresses
- 5.1.1 Define a pool of global addresses
- 5.1.2 Create an extended access control list to identify which inside addresses are translated
- 5.1.3 Establish dynamic source translation by binding the pool with the access control list
- 5.1.4 Specify inside and outside NAT interfaces
- 5.1.5 Verify the configuration
- 5.2 Configure Port Address Translation (PAT or Overload)
- 5.1 Configure Dynamic NAT with a Pool of Addresses
- 6 Troubleshooting
- 7 ISP Configuration
- 8 Final NorthCRT01
- 9 Final NorthCRT02
- 10 Final TestPC1
- 11 Final TestPC2
- 12 Final EVE topology
Learning Objectives
Upon completion of this lab, you will have:
- Configured NAT (Static and Dynamic)
- Distributed a default route via OSPF
Scenario
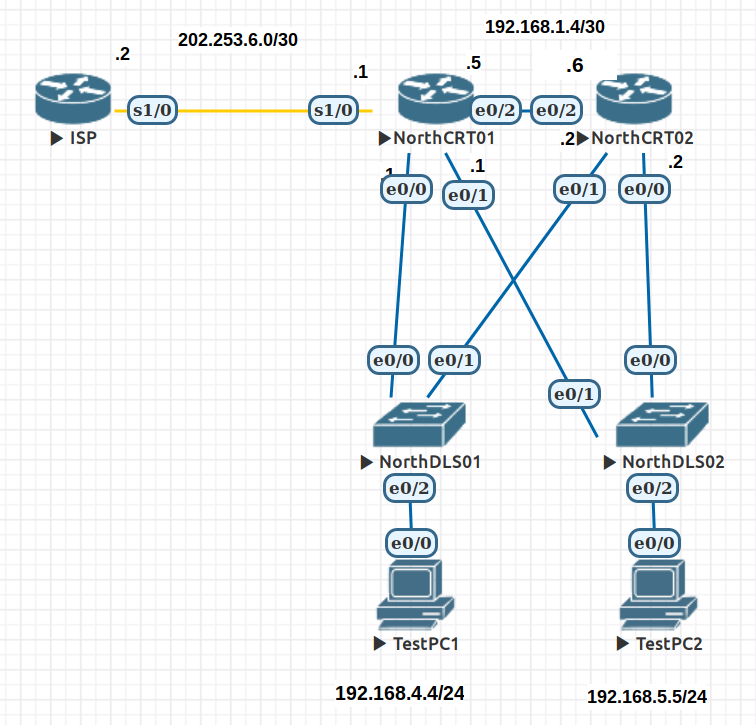
The topology shown represents an organisation's branch office. For the purpose of the lab the three layer design has been compressed. Example.com's LAN is simulated as is their WAN connection to their ISP. The ISP, Ethernet Switches and Test PC's are preconfigured. Your focus will be on the two core routers, where you will configure basic security and NAT to allow connectivity to an Internet host simulated on the ISP.
Steps
EVE
- Download the EVE lab topology from this link EVE NAT Static and Dynamic.zip
Note that the file contains both the starting config and a final config (solution). - Start the EVE server.
- Open a browser and enter the IP address of the EVE server.
- Import the topology
- Start all devices
Note: The two distribution layer switches (DLS) are acting as ordinary layer 2 Ethernet switches. Although they are capable of acting as routers we are not configuring them in this mode. They should be left in a default state.
Basic Connectivity
Using the details provided in the topology configure the following for your Core routers:
- Hostnames
- Interface
- IP addresses
- OSPF routing with a process ID of 1. This will be single area OSPF so all links will be in area o (zero).
Explanation of hosts
Although the hosts have a PC icon, they are in fact routers that we will use to simulate hosts in this lab.
Shown below is the configuration for PC1. Note that this has already been done for you:
TestPC1(config)#interface e0/0 TestPC1(config-if)#ip address 192.168.4.4 255.255.255.0 TestPC1(config-if)#no shutdown TestPC1(config-if)#ip route 0.0.0.0 0.0.0.0 192.168.4.1
Note the ip route performs the same function as the default gateway for a host.
Configure OSPF with a process ID of 1 and advertise all of the 192.168 links.
Hint:
router ospf <process ID> network <network address> <wildcard mask> area <area ID>
The wildcard mask merely defines which interfaces are participating in EIGRP. With some ACL knowledge you can now turn on all Interfaces with a single network statement. Alternatively you have more control if you use an individual statement for each interface. Check with you instructor if you don't understand how this works.
Reminder: The switches are configured as layer 2 only so no IP addresses need be configured. In this lab they act merely as access layer devices.
Before proceeding beyond this point make sure you have full connectivity and you can ping all devices and interfaces in your region.
Suggested testing commands:
ping show ip interfaces brief show ip route
Focus question: Why would we not advertise the S1/0 link using OSPF?
__________________________________________________________________________________________________________________________________
Network Address Translation (NAT)
Note that example.com's IP addresses are all part of the private 192.168.0.0/16 address range. These addresses are not routeable on the Internet as they are not uniquely assigned in only one location. Consequently example.com must use a global IP address when it wants to send and receive traffic from the Internet. These global addresses are assigned by the ISP and accompanied by a routing table entry on the ISP router that points to the organisations border router. In a small network (eg home ADSL) there may be only one global IP address. Specifically the IP address of the interface that connects to the ISP. In a larger network it is common for the ISP to grant a pool of global IP addresses to an organisation.
In this case of example.com the ISP has assigned a block of 256 addresses to the North region being: 202.253.1.0 /25
If we examine the ISP router configuration we see the following entries:
ip route 202.253.1.0 255.255.255.0 202.253.6.1 ip route 202.253.4.0 255.255.254.0 202.253.6.1 ip route 202.253.11.0 255.255.255.0 202.253.16.1 ip route 202.253.14.0 255.255.254.0 202.253.16.1 ip route 202.253.21.0 255.255.255.0 202.253.26.1 ip route 202.253.24.0 255.255.254.0 202.253.26.1 ip route 202.253.31.0 255.255.255.0 202.253.36.1 ip route 202.253.34.0 255.255.254.0 202.253.36.1
For each block of addresses reserved for their customer they have a static rout pointing to the customers router. They would then redistribute these static routes to other ISPs so that their customers network will be globally accessible.
ISP1 Link
example.com uses a serial connection to the ISP.
Before configuring NAT we must establish connectivity with our ISP. The following commands relate to your NorthCRT01 (border) router only:
ISP assigned static IP addresses.
North - 202.253.6.1 South - 202.253.16.1 East - 202.253.26.1 West - 202.253.36.1
- Make sure you can ping the ISP gateway assigned to the "North" region.
- You should be able to ping from NthCRT01 to the ISP
Focus question: Why can you not ping the ISP from the PCs or NthCRT02? __________________________________________________________________________________________________________________________________
Assigning and propagating a default route
- It is reasonable to assume that any networks not in example.com's routing table are Internet routes.
Therefore create a default route (Hint - it is a static route) on the NorthCRT01 border router that points to your ISP's router interface. Your ISP will use the .2 host address. When creating the default route use a next hop destination IP address rather than an exit interface such as S1/0.
- To allow all of the routers in your region to make use of this default route, have EIGRP propagate it for you.
Before adding the following commands, you should examine the routing table on NorthCRT02 to confirm there is no default route. After redistributing the route on NorthCRT01 you should see it is learned by NorthCRT02.
NorthCRT01(config)# router ospf 1 NorthCRT01(config-router)# default-information originate
Note: This is similar to the "default-information originate" that would be used in OSPF or RIP.
The ISP router has a loopback address configured as 1.2.3.4 this represents an Internet host with a global address. If you ping this address from example.com you will fail as the ISP cannot return packets to a private (192.168) address. If we want example.com packets to go out into the Internet they must now have global IP addresses. If we use private-addresses within our organisation, this implies we need to "translate" addresses as they leave and enter our network.
The ISP has reserved the following blocks of public/global IP address space for each of your regions:
North - 202.253.1.0 /24 South - 202.253.11.0 /24 East - 202.253.21.0 /24 West - 202.253.31.0 /24
The ISP will have a static route for these networks that points to your appropriate border router. A real ISP would propage customer networks throughout the Internet via the BGP (Border Gateway Protocol).
Note: In practice there is often a charge for the allocation of blocks of addresses such as this. There is also an administrative requirement that we justify the allocation. After all there is a shortage of IP version 4 addresses.
Focus question: Why can you still not ping the ISP from the PCs or NthCRT02? __________________________________________________________________________________________________________________________________
Hint: Apply the following command on the ISP router debug ip icmp and ping the ISP again while watching the ISP terminal output. If you still don't know why your ping is not working try show ip route on the ISP router. To really understand why we need NAT you really need to understand why you can't ping without it.
Configure Static NAT
Here you will statically map a public (global) IP address to a private IP address. This is necessary when you wish to make a server with your private addressing structure, available to the Internet. For this exercise we will pretend that PC1 is a server that we wish to make available on the Internet.
- Statically assign the last IP address (202.253.1.255) of your global IP address space for NAT to use to map packets to the private IP address of PC1 at 192.168.4.4. In this case we are using PC1 to simulate a server. For example a web server.
Note: All translation (NAT) configuration occurs at the border between private and global addresses. In our case this is the NorthCRT01 router.
NorthCRT01(config)#ip nat inside source static 192.168.4.4 202.253.1.255
- Specify inside and outside NAT interfaces. Before NAT can work, you must specify which interfaces are inside and which interfaces are outside.
NorthCRT01(config)#interface serial 1/0 NorthCRT01(config-if)#ip nat outside NorthCRT01(config-if)#interface e0/0 NorthCRT01(config-if)#ip nat inside NorthCRT01(config-if)#interface e0/1 NorthCRT01(config-if)#ip nat inside NorthCRT01(config-if)#interface e0/2 NorthCRT01(config-if)#ip nat inside
- Verify the static NAT configuration. From the ISP, ping the public IP address 202.253.1.255.
NorthCRT01#show ip nat translations Pro Inside global Inside local Outside local Outside global --- 202.253.1.255 192.168.4.4 --- ---
If you need proof that the pings are really being returned from PC1 execute the following:
TestPC1#debug ip icmp
If you ping the address again you will see the pings are being returned by PC1.
You can also verify that PC1 itself can access the Internet, now that it has a global IP address.
- Ping the Internet host (loopback on ISP) at 1.2.3.4 from PC1 to verify full Internet connectivity. In contrast this will not work on PC2 because there is no NAT translation.
Configure Dynamic NAT with a Pool of Addresses
While static NAT provides a permanent mapping between a single internal address and a specific public address (suitable for a permanent server), dynamic NAT maps private IP addresses to public addresses. These public IP addresses come from a NAT pool (Suitable for hosts needing outbound Internet access).
Define a pool of global addresses
- Create a pool of addresses to which matched source addresses are translated. The following command creates a pool named MY-NAT-POOL that translates matched addresses to an available IP address in the 202.253.1.1 - 202.253.1.127 range.
NorthCRT01(config)#ip nat pool MY-NAT-POOL 202.253.1.1 202.253.1.127 netmask 255.255.255.128
Create an extended access control list to identify which inside addresses are translated
NorthCRT01(config)#ip access-list extended NAT NorthCRT01(config-ext-nacl)#permit ip 192.168.0.0 0.0.255.255 any
Establish dynamic source translation by binding the pool with the access control list
A router can have more than one NAT pool and more than one ACL. The following command tells the router which address pool to use to translate hosts that are allowed by the ACL.
NorthCRT01(config)#ip nat inside source list NAT pool MY-NAT-POOL
Note the CAPITAL letter entries are not commands but references to lists and pools. It is best practice to make this clear and use capitals.
Specify inside and outside NAT interfaces
You have already specified the inside and outside interfaces for your static NAT configuration.
Verify the configuration
Ping the Internet (1.2.3.4) from PC2 and NorthCRT2. Then use the show ip nat translations and show ip nat statistics commands on NorthCRT01 to verify NAT. Your output may vary depending on where you ping from and how long ago you pinged. Remember this is dynamic and the translation is built and torn down as required.
NorthCRT01#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 202.253.1.2:0 192.168.1.6:0 1.2.3.4:0 1.2.3.4:0 --- 202.253.1.2 192.168.1.6 --- --- --- 202.253.1.255 192.168.4.4 --- --- --- 202.253.1.1 192.168.5.5 --- ---
As we are performing strict NAT you should find that each private address is mapped to a unique global address.
NorthCRT01#show ip nat statistics Total active translations: 1 (1 static, 0 dynamic; 0 extended) Peak translations: 4, occurred 00:17:49 ago Outside interfaces: Serial1/0 Inside interfaces: Ethernet0/0, Ethernet0/1, Ethernet0/2 Hits: 35 Misses: 0 CEF Translated packets: 35, CEF Punted packets: 0 Expired translations: 5 Dynamic mappings: -- Inside Source [Id: 1] access-list NAT pool MY-NAT-POOL refcount 0 pool MY-NAT-POOL: netmask 255.255.255.128 start 202.253.1.1 end 202.253.1.127 type generic, total addresses 127, allocated 0 (0%), misses 0
- To troubleshoot issues with NAT, you can use the debug ip nat command. Turn on NAT debugging on the NorthCRT01 router and repeat the ping from one of the other routers.
NorthCRT01#debug ip nat IP NAT debugging is on NorthCRT01# *Oct 20 05:14:56.388: NAT*: s=192.168.4.4->202.253.1.255, d=1.2.3.4 [35] *Oct 20 05:14:56.409: NAT*: s=1.2.3.4, d=202.253.1.255->192.168.4.4[35] *Oct 20 05:14:56.411: NAT*: s=192.168.4.4->202.253.1.255, d=1.2.3.4 [36] *Oct 20 05:14:56.433: NAT*: s=1.2.3.4, d=202.253.1.255->192.168.4.4 [36] *Oct 20 05:14:56.436: NAT*: s=192.168.4.4->202.253.1.255, d=1.2.3.4 [37] *Oct 20 05:14:56.457: NAT*: s=1.2.3.4, d=202.253.1.255->192.168.4.4 [37] *Oct 20 05:14:56.460: NAT*: s=192.168.4.4->202.253.1.255, d=1.2.3.4 [38] *Oct 20 05:14:56.484: NAT*: s=1.2.3.4, d=202.253.1.255->192.168.4.4 [38] *Oct 20 05:14:56.487: NAT*: s=192.168.4.4->202.253.1.255, d=1.2.3.4 [39]
Configure Port Address Translation (PAT or Overload)
In the previous example, what would happen if you needed more than the 128 public IP addresses that the pool allows?
__________________________________________________________________________________
By tracking port numbers, NAT overloading allows multiple inside users to reuse a public IP address. In this task, you will remove the pool and mapping statement configured in the previous task. Then you will configure NAT overload on NorthCRT01 so that all internal IP addresses are translated to the NorthCRT01 S1/0 address when connecting to any outside device.
Step 1: Remove the NAT pool and mapping statement
- Use the following commands to remove the NAT pool and the map to the NAT ACL.
NorthCRT01(config)#no ip nat inside source list NAT pool MY-NAT-POOL NorthCRT01(config)#no ip nat pool MY-NAT-POOL 100.200.1.1 100.200.1.127 netmask 255.255.255.128 NorthCRT01(config)#no ip nat inside source static 192.168.4.4 202.253.1.255
If you receive the following error message, clear your NAT translations and then remove the pool again.
%Pool MY-NAT-POOL in use, cannot destroy NorthCRT01#clear ip nat translation *
2: Configure PAT on NorthCRT01 using the serial 1/0 interface public IP address
The configuration is similar to dynamic NAT, except that instead of a pool of addresses, the interface keyword is used to identify the outside IP address. Therefore, no NAT pool is defined. The overload keyword enables the addition of the port number to the translation. Because you already configured an ACL to identify which inside IP addresses to translate as well as which interfaces are inside and outside, you only need to configure the following:
NorthCRT01(config)#ip nat inside source list NAT interface S1/0 overload
Verify the configuration
- Ping ISP from both of the test PC routers. Then use the show ip nat translations and show ip nat statistics commands on NorthCRT01 to verify NAT.
NorthCRT01#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 202.253.6.1:1 192.168.4.4:1 1.2.3.4:1 1.2.3.4:1 icmp 202.253.6.1:4 192.168.5.5:4 1.2.3.4:4 1.2.3.4:4 NorthCRT01#
NorthCRT01#show ip nat statistics Total active translations: 0 (0 static, 0 dynamic; 0 extended) Peak translations: 2, occurred 00:01:17 ago Outside interfaces: Serial1/0 Inside interfaces: Ethernet0/0, Ethernet0/1, Ethernet0/2 Hits: 28 Misses: 0 CEF Translated packets: 28, CEF Punted packets: 0 Expired translations: 3 Dynamic mappings: -- Inside Source [Id: 1] access-list NAT interface Serial1/0 refcount 0
Note that the inside global address is now the NorthCRT01's WAN interface address and it is being shared by the hosts inside the the organisation when devices need to access the Internet.
* * * END OF LAB * * *
Troubleshooting
show ip interface brief
Interfaces don't work if they are not up at layer 1 (administratively down) or if the layer 2 protocol isn't functioning correctly (protocol down).
show ip route
If a route doesn't appear in your routing table the router can't get to that network. The routing protocol is the mechanism that passes routes between routers. So if routes appear on one router and not on another router then you should look to the connectivity between the routers (ping) and the operation and configuration of OSPF.
If you have trouble getting to the Internet then you need a default route in your routing tables.
For your reference the following configurations should be present at the conclusion of the lab:
TBA
ISP Configuration
hostname ISP ! ! interface Loopback0 description simulates an Internet Address ip address 1.2.3.4 255.255.255.0 ! interface Serial1/0 ip address 202.253.6.2 255.255.255.252 ! no ip http server no ip http secure-server ip route 202.253.1.0 255.255.255.0 202.253.6.1 ip route 202.253.4.0 255.255.254.0 202.253.6.1 ip route 202.253.11.0 255.255.255.0 202.253.16.1 ip route 202.253.14.0 255.255.254.0 202.253.16.1 ip route 202.253.21.0 255.255.255.0 202.253.26.1 ip route 202.253.24.0 255.255.254.0 202.253.26.1 ip route 202.253.31.0 255.255.255.0 202.253.36.1 ip route 202.253.34.0 255.255.254.0 202.253.36.1 ! line con 0 logging synchronous line aux 0 line vty 0 4 password class login transport input none ! ! end
Final NorthCRT01
hostname NorthCRT01 ! interface Ethernet0/0 ip address 192.168.4.1 255.255.255.0 ip nat inside ip virtual-reassembly in ! interface Ethernet0/1 ip address 192.168.5.1 255.255.255.0 ip nat inside ip virtual-reassembly in ! interface Ethernet0/2 ip address 192.168.1.5 255.255.255.252 ip nat inside ip virtual-reassembly in ! interface Serial1/0 ip address 202.253.6.1 255.255.255.252 ip nat outside encapsulation frame-relay IETF frame-relay lmi-type ansi ! router osp 1 net 192.168.0.0 0.0.255.255 area 0 default-information originate ! ip nat inside source list NAT interface Serial1/0 overload ip route 0.0.0.0 0.0.0.0 202.253.6.2 ! ip access-list extended NAT permit ip 192.168.0.0 0.0.255.255 any ! end
Final NorthCRT02
hostname NorthCRT02 ! interface Ethernet0/0 ip address 192.168.5.2 255.255.255.0 ! interface Ethernet0/1 ip address 192.168.4.2 255.255.255.0 ! interface Ethernet0/2 ip address 192.168.1.6 255.255.255.252 ! router ospf 1 net 192.168.0.0 0.0.255.255 area 0 passive-interface Serial1/0 ! end
Final TestPC1
hostname TestPC1 ! interface Ethernet0/0 ip address 192.168.4.4 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.4.1
Final TestPC2
hostname TestPC2 ! interface Ethernet0/0 ip address 192.168.5.5 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.5.1 ! end
Final EVE topology
EVE lab topology fully configured: EVE - NAT - Final Configuration.zip