Difference between revisions of "Tunneling Services"
(Created page with "The point of this lab is to show you how you can tunnel services over an untrusted network. The tunneling mechanism that we are using in this lab is Point-to-Point Tunneling P...") |
|||
| Line 14: | Line 14: | ||
sudo apt install uml-utilities | sudo apt install uml-utilities | ||
sudo apt install pptpd | sudo apt install pptpd | ||
| + | sudo apt install net-tools | ||
Then, statically assign an IP address of 192.168.1.150 to the Ubuntu host that will act as the VPN server. You can use the GUI on Ubuntu for this. This interface will represent the external, Internet facing side of our companies VPN. | Then, statically assign an IP address of 192.168.1.150 to the Ubuntu host that will act as the VPN server. You can use the GUI on Ubuntu for this. This interface will represent the external, Internet facing side of our companies VPN. | ||
Revision as of 04:49, 27 August 2020
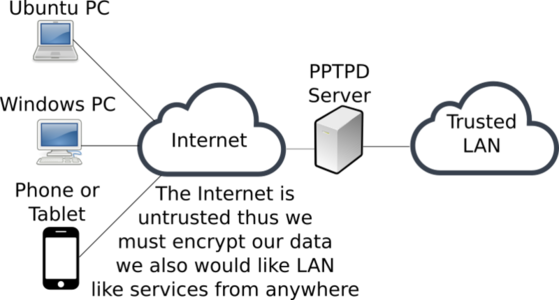
The point of this lab is to show you how you can tunnel services over an untrusted network. The tunneling mechanism that we are using in this lab is Point-to-Point Tunneling Protocol (PPTP). While it is not the most secure mechanism it does work easily on many mobile devices.
Have a close look at the physical lab setup that we will use to complete this lab, as well as the conceptual lab setup. If you are unsure about how the topology in this lab will map to the real world
Configuration
Start by installing the required Linux packages for the lab:
sudo apt update sudo apt install uml-utilities sudo apt install pptpd sudo apt install net-tools
Then, statically assign an IP address of 192.168.1.150 to the Ubuntu host that will act as the VPN server. You can use the GUI on Ubuntu for this. This interface will represent the external, Internet facing side of our companies VPN.
To do this in Ubuntu, right click the network icon in the top right and do edit connections. Once you have edited the profile, you will need to enable it by clicking on the network icon then auth eth0
Plug this Ethernet interface into your wireless AP. Ensure that you can ping your wireless AP at 192.168.1.1
We will now create our internal virtual interface. This interface and the associated subnet is going to represent the internal LAN that our remote users will have access to. You will have successfully completed the lab when your remote devices are able to ping 10.0.0.1 through your pptpd tunnel.
Create the internal LAN interface with:
sudo tunctl -t tap0
sudo ifconfig tap0 inet 10.0.0.1 netmask 255.255.255.0
Ensure that the interface has been created by typing:
ifconfig
Verify that you can ping it before moving on.
Configure the PPTPD server with:
sudo nano /etc/pptpd.conf
Uncomment and change the following lines to
localip 10.0.0.1 remoteip 10.0.0.234-238,10.0.0.245
Disable the logwtmp option by adding a # before it. The issue appears to have been logged as a bug here:
https://bugs.launchpad.net/ubuntu/+source/pptpd/+bug/1451419
Then have a look through:
sudo nano /etc/ppp/pptpd-options
This configuration should not need editing but it is interesting to look at as it describes the authentication and encryption parameters of your VPN
Edit the chap secrets:
sudo nano /etc/ppp/chap-secrets
This file follows the following format
<username> <IP> <users-password> <IP>
Edit it to look like:
# Secrets for authentication using CHAP # client server secret IP addresses student * student *
The asterisk characters mean any
As with all linux servers, once the configuration has changed, you must restart the service using:
sudo /etc/init.d/pptpd restart
Finally, any linux server/router that will be moving packets over different subnets needs IP forwarding enabled. You must edit the following file and replace the 0 with a 1.
sudo nano /proc/sys/net/ipv4/ip_forward
Connect your remote devices to the AP and ensure that they can ping the Linux PPTP server at 192.168.1.150. This wireless network really represents the Internet or any network that is insecure. Try to work out to VPN to 192.168.1.1. Remember that it it a PPTP VPN. Have a play with different PCs (unix and Win), ipads/iphones, droid phones/tabs.
Before connecting to a device, monitor the logs on the server with:
tail -f /var/log/syslog
The output may help you to debug any problems.
When you connect successfully you should see the following output.
May 3 14:20:13 ciscolabLI pppd[5139]: local IP address 10.0.0.150 May 3 14:20:13 ciscolabLI pppd[5139]: remote IP address 10.0.0.234
The remote IP address of 10.0.0.234 indicates the IP of your VPN device.
If you connect from a Windows or linux PC you should try pinging 10.0.0.1 and 10.0.0.150 from your 'remote' device
If you are connecting from a phone or a tablet, you may need to ping or nmap the device from your ubuntu server as some of these devices lack network troubleshooting tools. As you connect more devices add more usernames. Add more to the CHAP file:
sudo nano /etc/ppp/chap-secrets
Remember to restart the service
sudo /etc/init.d/pptpd restart
When you have multiple devices configured, you should be able to ping between them all, get the addresses from an ifconfig/ipconfig or from the output show in a
tail -f /var/log/syslog
Ensure that you are only connecting users with MSCHAP and MPPE 128-bit stateless compression
If your mobile device has gone to sleep it will not respond to pings.
Extra Notes for client configuration of PPTP
Android: intuitive
iOS: intuitive
Ubuntu:
- Go to network connections.
- You need to open the advanced options and select MPPE and allow stateful encryption.
- When you connect, do an ifconfig and check that a ppp0 interface was connected and ping the tun0 interface on the server
Win 7:
- Open network and sharing centre,
- Setup a new connection or network,
- Setup a dial-up or vpn connection to your workplace,
- no create a new connection,
- Use my Internet connection VPN,
- I will setup an Internet connection later.
- Wait for windows to tell you you cant do it,
- then click on the icon in the bottom right corner and connect to the VPN anyway
- ping the tun0 interface on the server to verify connectivity
Challenge
Try to authenticate to the PPTP server using the dd-wrt broadband routers as a client