SSID Hiding and MAC Filtering
In this lab, we will show the vulnerabilities of SSID hiding and MAC filtering. This should illustrate why you would never use either of these mechanisms for security purposes.
Contents
Lab Setup
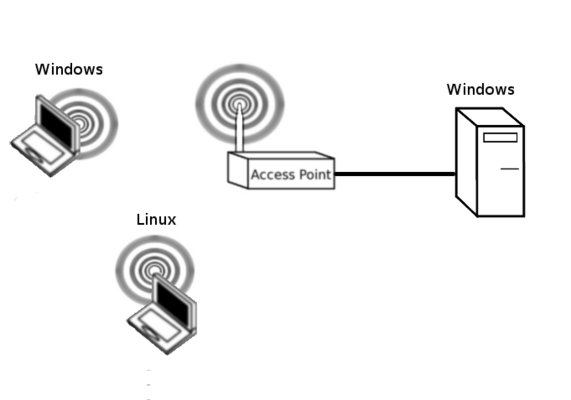
You should start by setting up a network as shown below.
AP Setup
We are going to start by hiding the SSID broadcast. Wireless networks are found/discovered by wireless clients in two ways; by using probe request messages and beacons. Both of these frame types contain the SSID. By hiding the SSID broadcast, the SSID, found in the beacon, is padded with zeros. Furthermore, the AP will not respond to probe requests which are sent by clients searching for surrounding APs. Hide the SSID under wireless->basic settings. Remember to save and apply. Once you have applied, your SSID should be hidden. You should find that you cannot connect to your AP without the SSID.
Both of the above mechanisms are bad security mechanisms. Both can be bypassed simply by monitoring the wireless medium using a special wireless mode called monitor mode and a network analysis tool called Wireshark. Once these values are known, MAC addresses can be changed with specific software and SSIDs can be manually entered. Later in the semester we will explore/show how these security mechanisms can be circumvented.
Wireshark
Open Wireshark with root. On the terminal, type
sudo wireshark
and start capturing on your wifi adaptor on PC1. Ping your access point over the link and ensure that you have captured these frames. Save your packet capture for later. What can you see? What is do you think might be missing?
Putting the wireless interface in monitor mode
Click the network icon in the top right and "Turn Off" Wifi. This will stop the OS from controlling our network device. Issue a:
david@chompsky:~$ sudo ifconfig -a
Identify which is your newly inserted wireless interface name (it should be the last one listed)
You can use one of the two methods below for putting your wireless card in monitor mode.
Method 1: the standard tools
Look for the wireless adaptor name in the output. On my computer, it was: wlx00c0ca84b9ab. Use the commands below changing the interface name to suit the computer in front of you.
sudo iwconfig wlx00c0ca84b9ab mode monitor sudo ifconfig wlx00c0ca84b9ab up sudo rfkill unblock all sudo ifconfig wlx00c0ca84b9ab up
Method 2: using Aircrack
On the command line issue:
sudo rfkill unblock all sudo airmon-ng start [interfacename] [channel]
If this works correctly then do another
ifconfig
You should have a new interface called mon0
Wireshark
Once you have setup your monitor mode interface you should open Wireshark:
sudo wireshark
Start capturing on your monitor mod interface. Remember that you can change the channel of your monitor mode adaptor by opening a terminal and typing:
sudo iwconfig wlx00c0ca84b9ab channel [Channel your AP is using]
You should notice that the beacons being transmitted by your access point have the SSID field filled with garbage. Look through these messages closely. Is it still possible to determine the SSID? Have a close look at the probe request and probe response messages when devices are connecting. Can you search for or filter for these messages?
Do you think this is a good security mechanism? Why/why not?
Change your MAC address
Note that you can also see all of the MAC addresses of connected stations. Look at your current MAC address with:
sudo ifconfig [interface_name]
Change your MAC address with:
sudo ifconfig [interface_name] down sudo ifconfig [interface_name] hw ether [MAC:ADDRESS] sudo ifconfig [interface_name] up
Take a look at your changed MAC address with:
sudo ifconfig [interface_name]
Hopefully, this lab should have shown why hiding the SSID and MAC address filtering are poor security mechanisms. You should also know and understand how easily they can be circumvented.